Defining Cybersecurity Events and Incidents
There is a ton of technical jargon out there that can be misconstrued, especially if some departments (like Information Technology or IT) have their own way of communicating. In the cybersecurity industry, it is often said, “all incidents are events, but not all events are incidents.” But what does this mean? There are various ways to go about handling a cybersecurity event or incident, but of first importance is to know the difference between the two!
Cybersecurity Event
Technology systems often classify all things as an ‘incident’, which is not correct. If it were, then your organization must be really unlucky, to say the least! Anyways, an event is a potential or suspected security threat. These occurrences can be benign but bear watching, or malignant.
Cybersecurity Incident
Although events should be taken seriously, an incident is more urgent due to the negative impact it can have on an organization. Incidents, therefore, are highly probable, or confirmed, security effects.
Key Differences
Organizations may deal with thousands of events daily. Not all of them will turn into an incident. The differentiating factor is data! Unless sensitive information is compromised, an incident has yet to occur.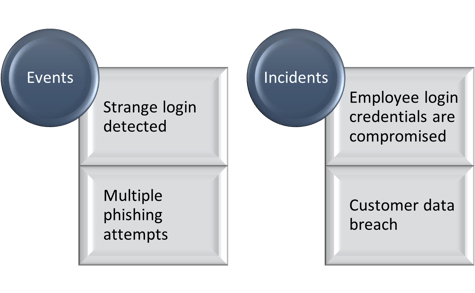
Did something really happen? Of course, for an event or incident to ensue, something must take place, but the occurrence is not always cause for panic. Case and point: an employee left their office door open after a long day’s work. This is not a best practice as it leaves the door open (pun intended) for a potential security breach; luckily, nothing happened, making it an event. If someone were to have entered the employee’s office after hours and stolen valuable information, this would be classified as an incident; the employee would be able to confirm the following day, that a data breach has occurred. As a reasonable standard, even if you cannot prove something did not happen, assume something did and alert whoever is necessary.
Plan for the worst, hope for the best
Incident response can result in lessons learned. Events give room for error to occur without the unwanted chaos, while incidents result in having to clean up a mess of (usually continuous) mistakes being made. Being able to respond/handle either of these activities is very important. Start with the following steps!
- Create a Security Incident Response Plan
- Run tabletops so that stakeholders know their role; including Marketing and HR (not just IT)
- Perform traffic analysis of the network
- Monitor employment activity, checking for any suspicious behavior(s)
- Understand the levels of event/incident classification
